Email Encryption Retarus Email Encryption
Rely on top-quality service for encryption of your email communication. Retarus Email Encryption enables you to comply with applicable data protection regulations, safeguard valuable know-how and protect confidential information.
Encrypted & Confidential
Unencrypted emails pose a major security risk. They can be covertly read at any time during their transmission—just like a postcard. Retarus Email Encryption protects the confidentiality of your communications. That’s because this encryption system protects both personal data and your valuable company know-how. It also ensures compliance with the applicable data protection guidelines.
%
%
Your Benefits
Secure
Transparent
Efficient
Scalable
Mobile
Compliant




How Good Is Good Enough for You?
Retarus Email Encryption Features at a Glance
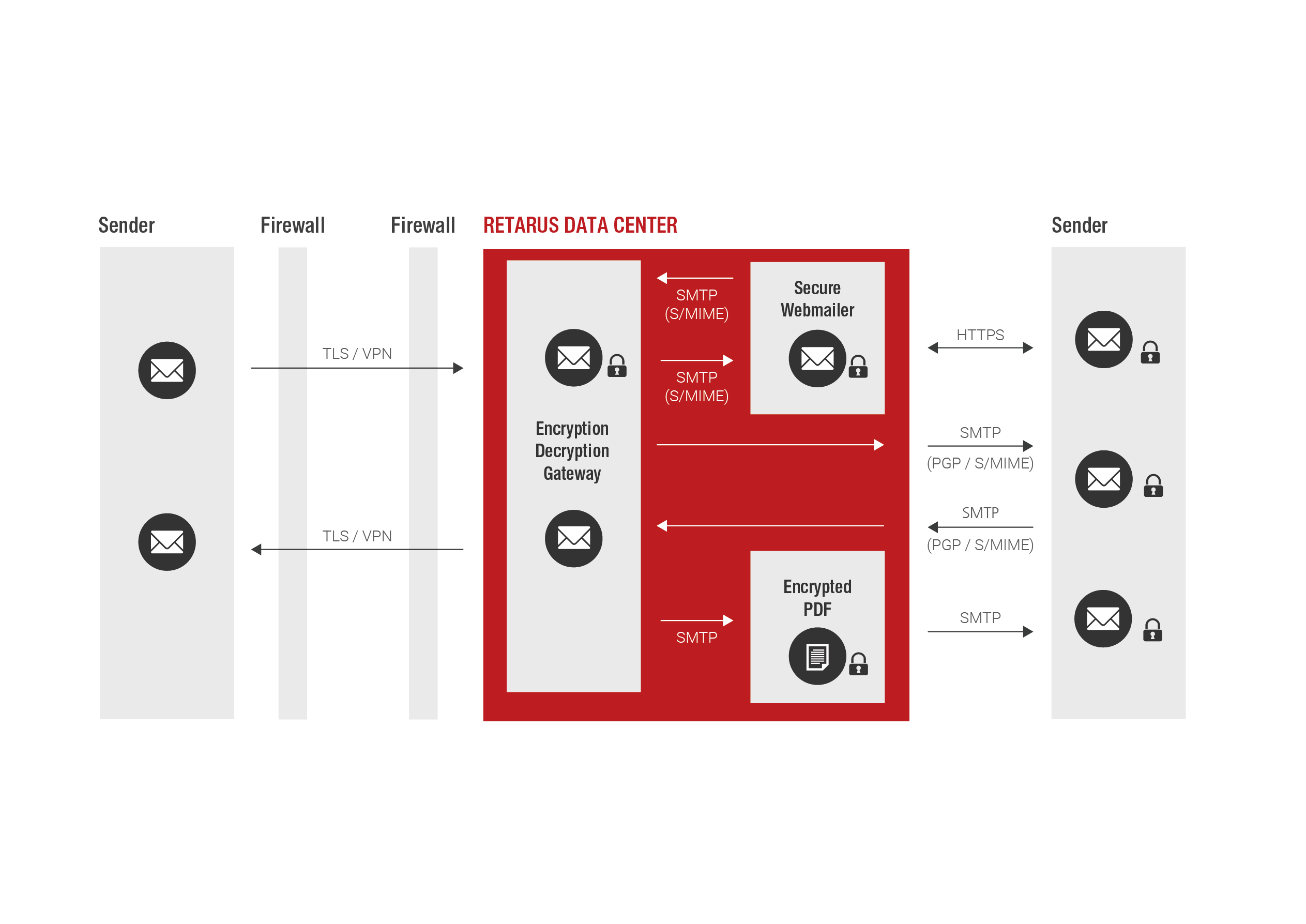
Emails are identified in Retarus data centers, fully encrypted using customer-specific rules, signed as needed and sent securely to the recipient. This means that the email and all of its file attachments are encrypted.
- Compatible with any SMTP-based email system (e.g. Microsoft 365, Google Workspace, Microsoft Exchange, HCL Notes Domino)
- Complete key management by Retarus: create, distribute, and manage all keys
- Easy adoption of existing PKIs (public key infrastructures)
- Gateway-based S/MIME and PGP encryption
- Full support of the X.509 v3 standard including own certificates
- Full support of the OpenPGP standard
- Automatic or user-initiated signature of outgoing emails
- Ability to include internal company encryption policies
- Centralized and flexible set of rules for emails that need to be signed
- Filters for viruses and spam despite encryption
- TLS connection to the Retarus Enterprise Cloud
- Optional VPN connection for secure and confidential communication over the "last mile"
- Web email portal or password-protected PDF for encrypted communication with recipients without their own encryption solution
- Company-wide standardized solution that can be expanded as needed
- No software and hardware installation required
- User Synchronization for Encryption (USE) feature automates management of encryption users, groups, associated certificates/keys, as well as organization-specific policies.
Add-on
Easily Meet Compliance Requirements.
With Retarus Email Archive you can archive your email correspondence tamper-proof and in real-time. Highly-secure Retarus data centers ensure that communication remains unalterable and protected thanks to the four-eyes-principal preventing unauthorized access. And emails can be retrieved in seconds, even with high archive volumes. This enables you to reliably ensure compliance with the most stringent regulations and international data protection guidelines, such as the EU General Data Protection Regulation (GDPR).
Retarus Email Encryption ensures your business communication always remains confidential. Whether encryption-based using customary standards or password-based via secure webmailer. The sophisticated encryption system protects not only your valuable company expertise, but your personal data as well. Ease of use and automated encryption management included.
Retarus Data Loss Prevention ensures that confidential information, such as customer, production, or design data does not end up somewhere outside of your company’s network. Externally addressed emails are checked systematically using pre-defined criteria and withheld in case of doubt. Furthermore, specific rules regarding permitted recipients can be defined at the mailbox level.
Contact an Expert Now