The protection of sensitive email communication is of vital importance for companies. Or so you might think. However, email encryption is often perceived to be time-consuming and overly complex. Consequently, it is simply not used.
The problem is known well enough. Sending an email via the Internet is analogous to sending a postcard. Anyone involved in the transmission process can read it without being noticed. Nevertheless, employees seldom encrypt their emails. It’s too complex, too technical. End users often get hung up on the basics, let alone sparing a thought for private or public keys. On the admin side, the situation is hardly better. The effort required for implementation and management seems too huge. As a result, they simply forgo encryption. This situation is far from acceptable for companies. Only well-designed email encryption protects personal data and valuable company know-how, while safeguarding the confidentiality of a company’s business communication.
Uncomplicated email encryption – also for recipients lacking their own encryption solution
It is highly advisable to opt for a gateway-based encryption solution which runs automatically in the background. This enables employees to encrypt outbound emails directly in their email client, for instance by simply clicking on a lock symbol. Even if the recipient is not using their own encryption solution, a good encryption solution will make the email available via a secure webmail inbox.
What’s more, customer-specific rule sets can be used to specify that emails sent to a specific communication partner or domain should always be encrypted.
High administrative effort is a deterrent
The high demands posed by email encryption often discourage IT departments. Among other things, certificates must always be kept up to date or assigned, for example when new employees are hired or leave the company. This implies taking into account both the regulations imposed by communication partners as well as the company’s own compliance requirements.
Simplified administration thanks to automation
Synchronization with the company’s directory service (e.g., Retarus User Synchronization for Encryption) allows the admin to manage individual users, groups, keys, or certificates and policies independently. Based on these customer-specific rules, confidential messages – including all file attachments – are automatically encrypted. The service also facilitates the synchronization of S/MIME and PGP keys.
Uncomplicated key management
Administrators are notified immediately via email about the status of the synchronization and the keys which have been generated. In this way, IT managers retain full control over the keys used. In particular, large enterprises with many users, IT system houses, and distributors are able to reduce their manual workload and error rate significantly.
Audit-ready archiving of encrypted emails
Business emails additionally need to be stored in an audit-ready, legally compliant manner. To ensure this, Retarus Email Encryption decrypts inbound emails centrally by way of a cloud platform, before they are encrypted again using a master archive key and stored away safely. This ensures that messages are also readable if the respective private key no longer exists at the time the message needs to be accessed.
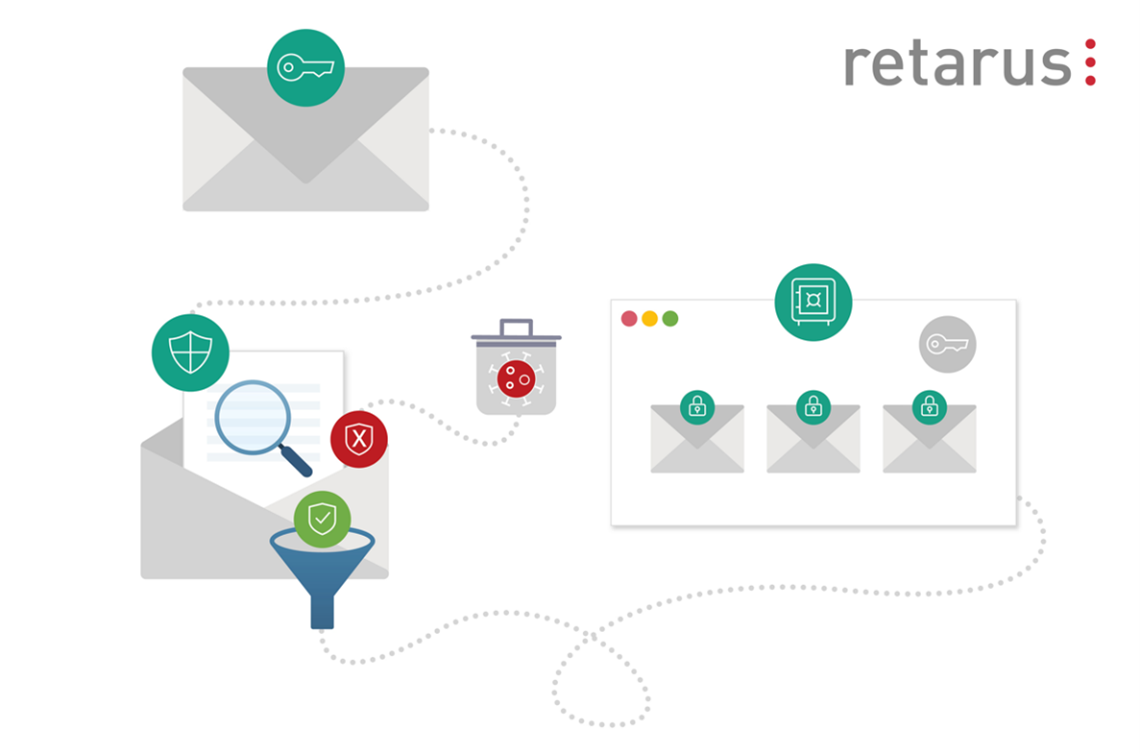
All-encompassing email protection from a single source
In addition to encryption, email security plays a critical role in safeguarding confidential data from unauthorized access and providing the best possible email communication protection. It’s essential to check both inbound and outbound emails for malware, spam, and phishing. Ideally, companies should opt for a European provider who is not subject to the US Cloud Act and processes their data in redundant data centers located in Europe.
Checklist – What constitutes the ideal email encryption solution?
- Email encryption with S/MIME, PGP, and OpenPGP
- Covers all commonly used standards
- Full encryption of all messages and attachments
- Supports the X.509 v3 standard fully, incl. own certificates
- Automatic signature on outgoing messages
- Web portal for recipients lacking their own encryption solution
- VPN connection to European data centers
- Easy implementation without needing to install hardware or software
- Centralized management of all internal and external keys
- Compatible with all SMTP-based email systems
- Easily comprehensible for end users
- No user training necessary
Find out more about Retarus Email Encryption on our website or directly from your local Retarus representative.