After a break in transmission of roughly half a year, the devious trojan known as Emotet is now active again and flooding the inboxes of companies and authorities with deceptively genuine looking emails which are also highly dangerous.
Since the end of July, the experts at the Retarus Threat Intelligence unit have been registering an almost constant barrage of Emotet attacks. The treacherous thing about Emotet emails is that they at first glance appear to have been sent by a real colleague, make reference to previous email conversations, and recently even started adding documents from earlier conversations as attachments. Creating this illusion of familiarity lowers the threshold for the recipient to click on the link included in the text – with disastrous consequences.
Emotet mostly uses MS Word documents contaminated with macro viruses to infect IT systems. The creators of the malware, and those looking to profit from it, store the malware on a constantly alternating series of unsuspicious looking servers. When someone has been fooled into opening one of these files and activating the macros it contains, the malware reads the address book and emails from Microsoft Outlook (also known as “Outlook harvesting”) and uses the information to generate more malicious emails to recipients in the network under attack. Emotet is moreover able to download further malware, for instance to snatch login credentials or gain remote access. The general aim of the malware is to paralyze the company’s entire IT network and/or to blackmail the victim to make ransom payments.
How can you protect yourself from Emotet?
There is no safeguard that can provide you with 100% protection from Emotet, in no small part because the polymorphous malware, first discovered in 2014, keeps changing and evolving due to constant development. A powerful email security service combined with the appropriate sensitization of users, however, goes a long way towards repelling the malware in many cases, and in case infection occurs, contain it and limit the impact.
It is worth noting that Retarus’ portfolio of services includes the groundbreaking post-delivery protection service Patient Zero Detection®, which has been patented in all relevant markets. This service makes it possible to detect malware and harmful hyperlinks in emails which have already been delivered as soon as the corresponding patterns have become available for one of the four scanners deployed in Retarus’ AntiVirus MultiScan, allowing the service to alert recipients as well as administrators about the danger.
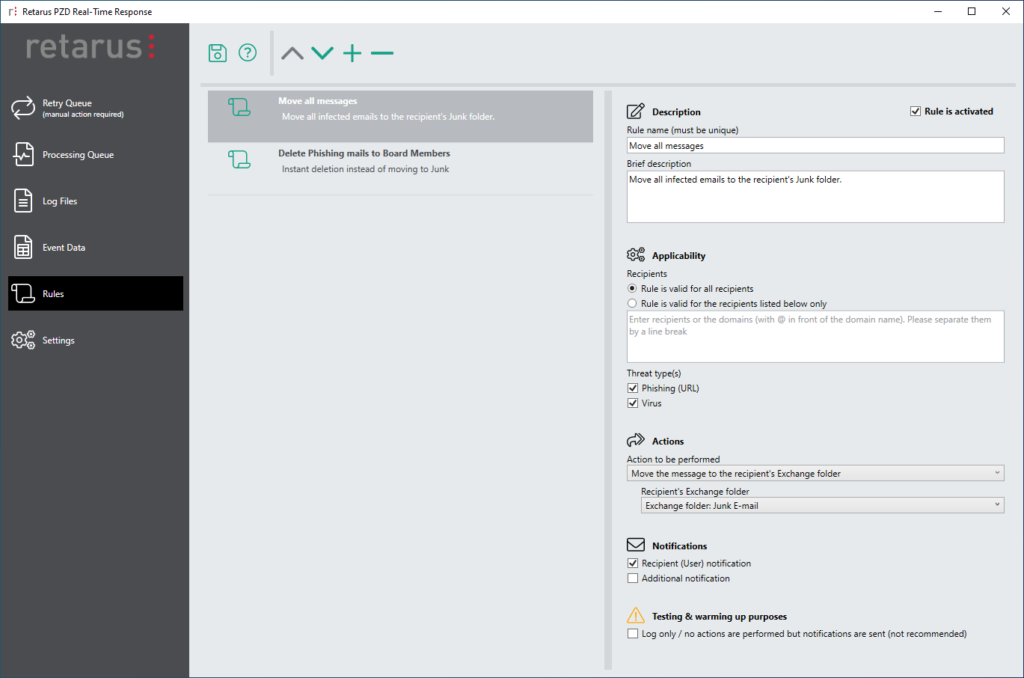
PZD Real-Time Response goes a step further. With this software for exchange environments, the malware discovered by the Patient Zero Detection® service can be processed according to a set of rules, meaning that potentially dangerous emails can be identified in a user’s inbox and then automatically moved to another location or deleted. Should a system become infected with Emotet, both of these tools could simplify mitigation and forensics tremendously.
Infected computers need to be disconnected from the network without delay
It’s essential that computers infected with Emotet be disconnected from the company network and the internet as quickly as possible, both to prevent the infected mail clients from spreading the malware within the company network and downloading further harmful payload from the web. The malware itself is programmed and installed so deviously, concealing itself so deeply within the system that you are best advised to wipe the affected computers clean and set them up again from scratch with a new standard image.
To ensure that our users are spared this ordeal, we would like to strongly recommend our free Anti-Phishing Guide, which contains a wide range of useful tips for handling emails wisely. You are welcome to download our little booklet in five languages and distribute it amongst your employees.

More information on Retarus’ Secure Email Platform including Patient Zero Detection® and PZD Real-Time Response is available on our website or directly from your local Retarus representative.




