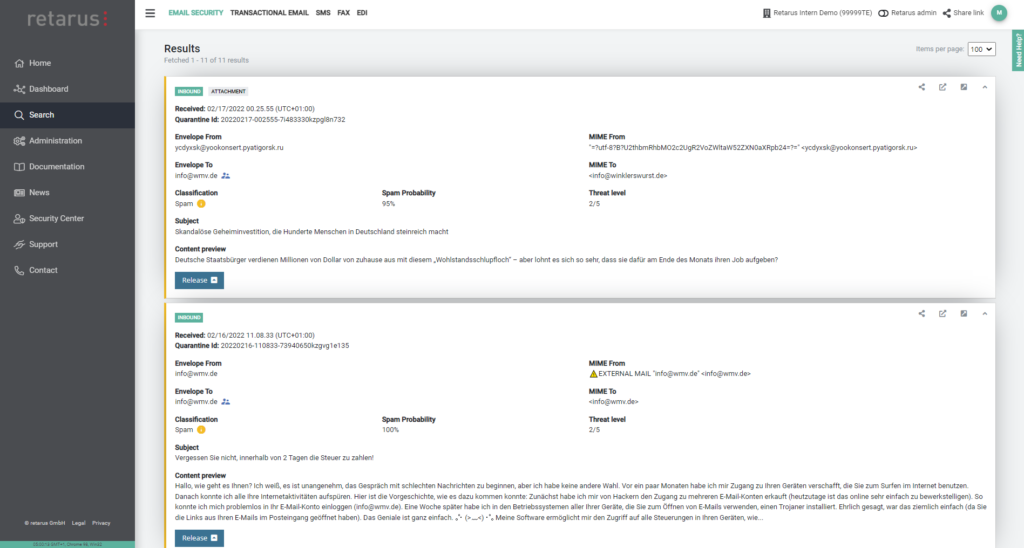
The comprehensive, powerful search options offered by Retarus Email Live Search make it possible for administrators to always track which email security filters and rules have been applied to each message. By way of the user-friendly, browser-based myEAS Portal, the search provides detailed results in real time, allowing remarkably fast analysis and IT forensics. Should a message go missing, for instance, this also allows support staff at the company or the Retarus partner to provide end users with detailed information about its current whereabouts without undue efforts.
New tracking points allow behind-the-scenes insight
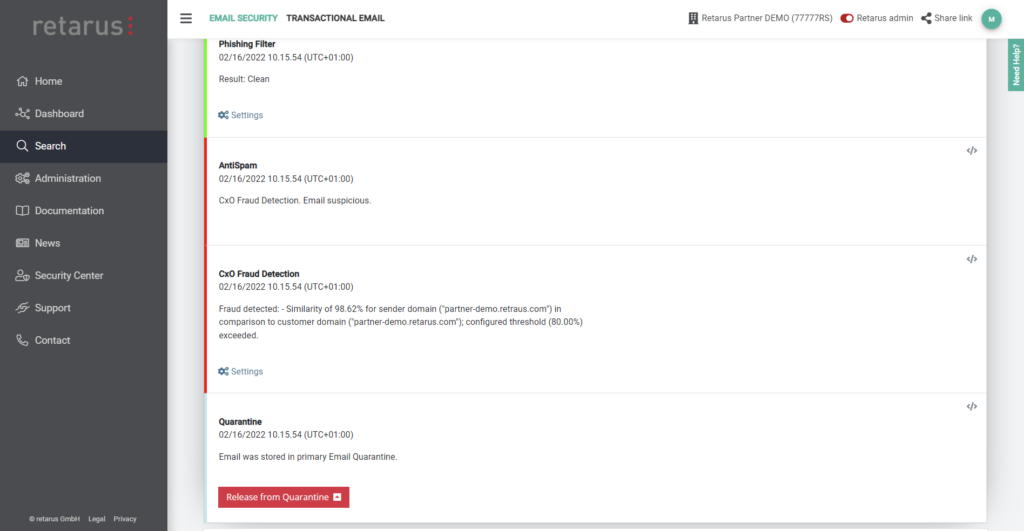
The search options and depth of detail are continuously expanded and enhanced by our team of developers. In just one of our recent developments, users now have access to a whole raft of additional insights (tracking points) related to our CxO Fraud Detection filtering feature. In this way, Email Live Search now transparently provides information about which algorithm has been applied to each message while the filter was operating. This provides helpdesk staff with valuable additional information for processing tickets and support requests.
Detailed analysis: Which vector of attack was employed?
A little background on this topic: In the course of the CxO Fraud Detection service, the messages are analyzed by means of numerous different mechanisms. Each of these provides a certain percentage of fraud probability, which is measured against the probability threshold that has been configured – in order to place the message in quarantine if necessary. While all these algorithms are designed to detect bogus email senders, they each target a different spoofing technique. Ultimately, knowing which vector of attack was employed also helps admins and partners to identify errors in their own configurations and fine-tune the corresponding threshold.
In addition to the screening of SPF Records, the checks focus on attack techniques such as the use of deceptively similar-looking domain names (e.g. by substituting individual letters) and use algorithms to identify special character sets (e.g. the use of Cyrillic letters that resemble ASCII characters). Other checks include verifying whether attackers may be pretending to use the recipient’s own domain or a colleague’s name, although the email actually originated outside the organization’s infrastructure.
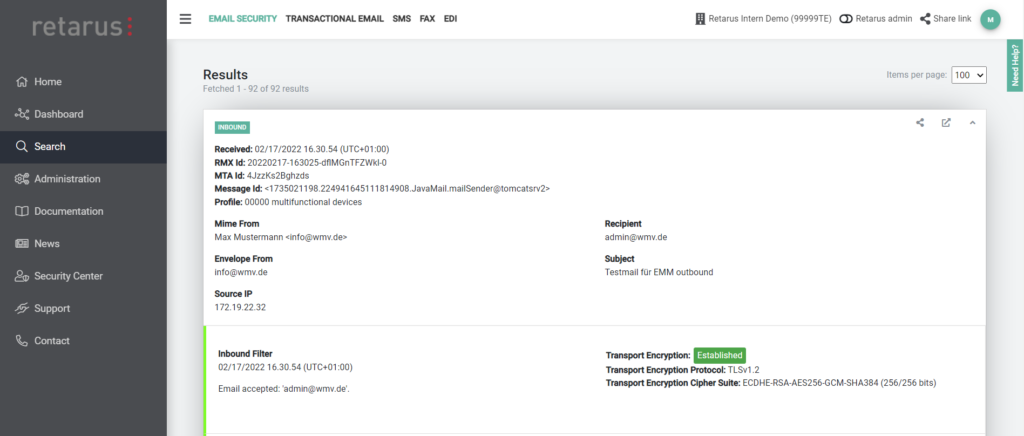
Detailed information on correct TLS encryption at message level
Even beyond the filtering results, Retarus increases transparency for admins and those responsible for IT security. It’s now possible to check each message individually within myEAS to determine whether it has been transmitted securely and properly using TLS encryption. For each transmission direction, the information is made available separately for each stage. In the inbound channel, this means securing the path from the internet to the Retarus Secure Email Platform, as well as the transmission from there to the customer’s infrastructure. The same applies equally in reverse for the outbound channel (customer > Retarus > internet).
Simplified admin access to the user quarantine
While myEAS serves as the central admin portal and provides detailed technical insights, admin access to the user quarantine was also recently optimized. Helpdesk workers with the requisite user rights are now given direct insight into the personal online quarantine portal of the individual end users, allowing them to provide assistance from the user perspective – such as releasing emails from quarantine or making changes to the settings.