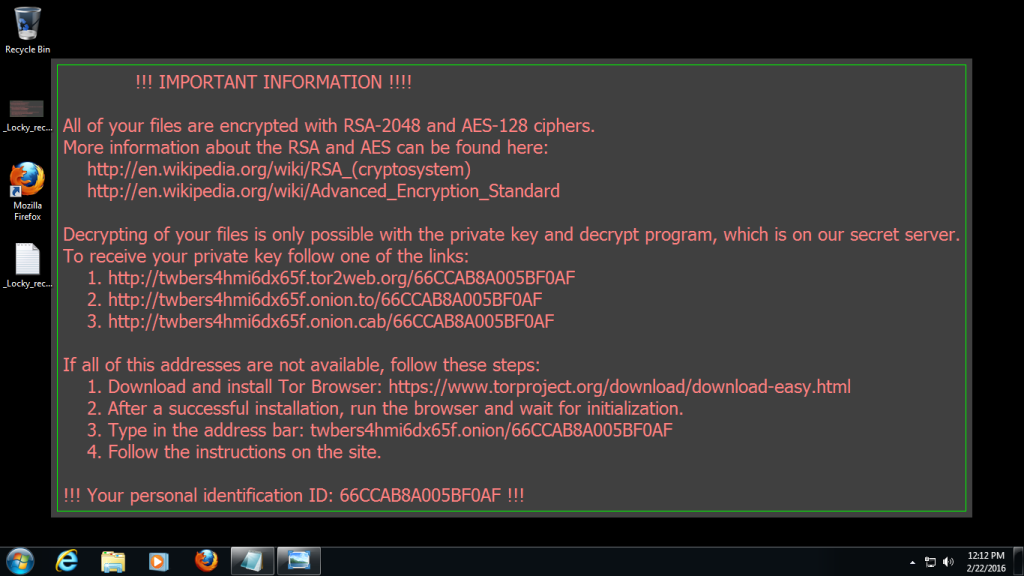
70 % of all companies previously held to ransom by perpetrators of a ransomware attack ended up paying the ransom demanded in order to regain access to their data.
This the result of a study just published by IBM. In comparison, more than half of all consumers surveyed said they would be unwilling to buy back access to their data if it had been encrypted by cyber criminals. Which is hardly surprising – after all, the data held by companies is usually more valuable than data stored on PCs in the private domain. However, this picture changes somewhat when consumers are asked about specific types of data. In this survey, 54 percent said they would pay to have their financial data returned to them. A slightly higher proportion – 55 percent – said they would give in to ransom demands for digital family photos (although this figure drops to just 39 percent among respondents who don’t have children).
A quarter of participants in this US study stated that, depending on the type of data involved, they would be willing to hand over between 20,000 and 50,000 dollars to buy back access to it. In Germany, ransomware attackers usually demand several thousands of euros from the companies they target, as reported by “heise online”. However, German companies are less willing to pay these ransoms than their US counterparts. This may partly be due to the fact that the FBI this year advised victims of ransomware attacks that it’s preferable to give in to ransom demands (although this recommendation has since been watered down somewhat).
It would appear that Germans view their data as being of less value by comparison. On average, victims of ransomware attacks in Germany paid the equivalent of 227 dollars. In Great Britain, this figure was more than twice as high at 558 dollars. Danish (446 dollars) and American (350 dollars) victims would also dig deeper into their pockets to unlock their encrypted data. However, some of the latest ransomware doesn’t even require payment of a ransom. One example is “Popcorn Time”, which, according to “ZDNet”, also offers the alternative option of infecting two more hosts to unlock your own data, and thus avoiding payment of the ransom by bitcoin transfer – in other words, this malware uses a perfidious type of “referral system”.
In any case, companies need to protect their computers from ransomware and other malware attacks. In addition to using an up-to-date scanner at the endpoints, e-mail postboxes, which are still a main point of entry for viruses and other malicious software, can be secured using a managed cloud service like Retarus E-Mail Security. Our brand-new “Patient Zero Detection®” option is even capable of retrospectively detecting the individuals to whom ransomware or other malware (new and so still as-yet-unknown) has already been delivered. More information on this topic is available directly from your local Retarus representative.