Every email user has encountered such messages in their own inbox – notifications from a “mailer daemon”, informing them about emails that could not be delivered. Mailer daemon is the designation used for a program which is responsible for delivering emails. Should the delivery fail for some reason, the daemon sends back a corresponding error message. The sender shown in the “From” field of such notifications usually follows the pattern mailer-daemon@servername.com.
Concrete instructions exert pressure on recipients to act
Nothing out of the ordinary, so far? It is precisely these everyday messages that scammers are now increasingly seeking to exploit, as the security experts at Retarus have recently discovered. As far as the layout, sender and subject lines are concerned, these emails resemble the genuine “message undeliverable” emails very closely. The text of the message, as is typical for these types of phishing emails, exerts pressure on the reader to take action. The recipient is informed that a number of emails could not be delivered and is advised to take action to rectify this problem. The link contained in the message, which purportedly allows the target of the scam to view the messages which have been held up, deliberately aims to arouse the recipient’s curiosity. Of course, hiding behind the link is not the expected email folder, but a phishing site with its sights set on committing fraud.
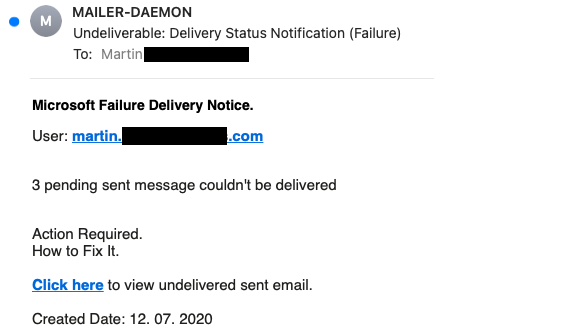
Genuine email address and reference to Microsoft aim to create impression of trustworthiness
The tricky thing about the emails increasingly cropping up at the moment is that the text makes direct reference to the Microsoft system as the sender, and mentions the correct email address of the potential victim again as the user name within the text of the message. The linked URL also takes up this address to suggest authenticity. What’s more, it also employs TLS transport encryption so that it can use the https:// prefix to pretend it is trustworthy, when in fact it is anything but secure.
Email security services help block phishing URLs
Retarus Email Security detects these kinds of scams using more than one approach. With the Time-of-Click Protection service, the URLs contained in emails are rewritten by default and checked against continually updating phishing databases at the time the link is clicked on. Only once this test has been passed, is the user forwarded to the destination page. Should the URL be classified as suspicious, the user receives a warning to this end in the browser.
And with the patented Patient Zero Detection, Retarus identifies suspect messages even when the links included in them are only identified as potentially harmful once the emails have already been delivered.
Regularly sensitizing users remains essential
As no email security solution can provide 100 percent protection from phishing attacks, it is essential for companies to sensitize their users regarding these threats on a regular basis (to raise user awareness). The following instructions for dealing with inbound messages have proved to be successful in averting phishing attacks:
- Avoid clicking on links in suspect emails (this includes unsubscribe links, with which you are only confirming the existence of your email address).
- Never open/download attachments from suspicious emails (malware).
- Do not answer suspect emails or forward them to others.
- Never enter your user name, passwords or any other personal details on untrustworthy websites.
- If you doubt the authenticity of an email, check back with the purported sender in person or by phone. In cases such as the “mailer daemon” message described above or similar system notifications, get in touch with the IT administrator/support at your organization.
To heighten awareness about fraudulent emails, Retarus has compiled these and many other valuable tips into an easy to understand “Anti-Phishing Guide”. You can download the guide for free in five languages from our website and share it with your employees.




