The need for more IT security has never been more apparent. We are increasingly opening ourselves up to the globally networked world – to communicate with each other, to trade, and to work together. Yet the more we open up, the more vulnerable we become, as made evident by the recent attacks in early March on organizations using Microsoft Exchange Server. A hole in the Exchange environment’s security initially led to attacks in the USA. It was not long before the hackers started launching attacks in Europe as well.
The security mechanisms offered by inflexible on-premises infrastructures or the usual cloud office solutions are often insufficient in protecting your organization and combating such attacks. For the protection they crucially require, companies are better advised to look to flexible cybersecurity services which are focused on email security and the increasingly prevalent Microsoft 365 Security.
How to ensure that security vulnerabilities in Exchange do not become a problem: Zero Trust as a strategy
The Zero Trust concept originates from the assumption that you should fundamentally not trust anyone or anything – not even yourself. The Zero Trust model was already formulated and recommended by Forrester twelve years ago for digital ecosystems. Zero Trust prescribes a basic principle of mistrust as a way of ensuring that maximum security can be achieved.
The example of the attacks on Exchange servers mentioned above illustrates that security mechanisms provided by on-prem or one-vendor approaches are insufficient for ensuring adequate protection for business communication. A secure, global exchange of information can only be accomplished by opting for modular and integrated ecosystem approaches. Outdated, insular solutions or simply pulling up the drawbridge by isolating the network is no longer enough. Modular platforms are best suited for enabling the selection of various components and meshing them together to achieve the highest possible degree of security for modern communication traffic.
Gartner says, “Traditionally, security products architectures have been built on proprietary ecosystems with minimal built-in integrations across different providers and products. This silo approach has been reinforced by end users‘ strategies focusing on best-of-breed capabilities from specialist providers. Digital transformation initiatives will increasingly require solutions that support deployment of more dynamic and effective controls across disparate environments and ecosystems. The emergence of approaches such as passwordless authentication and decentralized identity are examples of new security answers to the need of having security more localized and decentralized.” 1
Cloud trend in the pandemic fuels demand for appropriate security solutions
The trend towards the cloud has been accelerated by the COVID-19 pandemic, as evidenced by a recent IDC study:
- The acceptance and opportunities of the cloud are both set to grow continuously to reach a forecast market value of 1 trillion US dollars in 2024.
- Worldwide spending on security is expected to grow by 8.1 percent on average in the period from 2020 to 2024.
A growing number of companies are now deciding to move over to the cloud office services offered by Microsoft or Google. According to the Zero Trust principle however, companies using these services should be careful not to rely exclusively on a single cloud office solution and its integrated security mechanisms. It is advised that companies employ additional modern security technologies and services offered by third-party providers. Many companies have chosen this route already. A recent Gartner study2 shows:
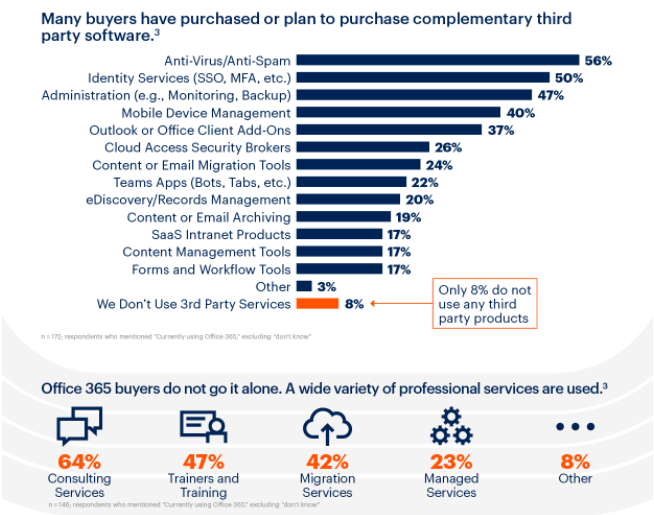
As it can be seen from the Gartner graphic above:
- 56 Percent of those who have purchased Microsoft Office 365 are using or planning to use third-party anti-virus/anti-spam solutions.
- 24 Percent of the participating companies are using or planning to use additional content or email migration tools.
- An additional 19 percent are using content or email archiving products offered by third party providers.
- In total, only 8 percent are not currently relying on third-party services.
Zero Trust thanks to a modular Secure Email Platform
Most harmful attacks make their way into the company network via email. However, since the GDPR came into force, the sharing of sensitive data – especially via email – is now afforded special protection. For this reason, it is highly recommended to take a best-of-breed approach, which consciously relies on technologies from a range of providers and takes the various dimensions of email into account.
The following dimensions should be considered when selecting a modular Secure Email Platform:
- Basic protection from DDoS attacks through multiple, intelligent filtering and anti-virus software
- Advanced Threat Protection (ATP) to safeguard against highly sophisticated, intelligent attacks (for instance, through sandboxing, intelligent and automatic pattern recognition, and intelligent traffic handling)
- Post-delivery Protection to render dangerous links and hacker attacks harmless, even after they have passed the firewall
- Information Protection with state-of-the-art encryption technologies, archiving, and information protection frameworks to protect sensitive information such as personal data, company secrets, or patents
- Compliance and strict adherence to legal provisions and regulations with the aid of audit-ready, verifiable control mechanisms
Third-party providers such as Retarus provide security services that complement Microsoft 365 substantially in these aforementioned dimensions.
More details about the Retarus Secure Email Platform can be found here or from your local Retarus contact person.
1) Gartner, Emerging Technologies: Defining Composable Security, Dennis Gaughan, April 20, 2021. See also Smarter With Gartner, “Gartner Keynote: The Future of Business Is Composable”, October 19, 2020,
2) Gartner, ‘Infographic: How Tech CEOs Can Work With (Or Compete Against) Microsoft Office 365’, Craig Roth, October 26, 2020